![]() Most cloud services tell you that their data stores are safe, that your data is encrypted in transit and on their drives, that employees don't have access, etc. For the vast majority of the stuff I store in the cloud, this is more than good enough for me—the data isn't overly sensitive, and if someone were to hack their way in, all they'd get are a bunch of work and personal writing files and some family photos.
Most cloud services tell you that their data stores are safe, that your data is encrypted in transit and on their drives, that employees don't have access, etc. For the vast majority of the stuff I store in the cloud, this is more than good enough for me—the data isn't overly sensitive, and if someone were to hack their way in, all they'd get are a bunch of work and personal writing files and some family photos.
For other files—primarily financial and family related—those assurances just aren't enough for me. But I still want the flexibility and security that comes from having a copy of these files in the cloud. So what's a paranoid user to do to take advantage of the cloud, with added security, but with a minimum of hassle?
The solution I came up with involves using local encrypted disk images and a shell script. Using this script (and some means of scheduling it), you can automatically encrypt and back up whatever files you like to a cloud service.
My how-to assumes you have the following:
- A selection of files you'd like to regularly save on a cloud service, and these fles are not normally encrypted on your Mac.
- An account with a cloud service such as Dropbox or Copy. (Referral links; I get some free space if you register.)
- Your cloud service synced to a local folder on your Mac—most all do this by default.
- An encrypted disk image of sufficient size to hold the files. Here's how to create one. My script assumes you set the Image Format to "sparse bundle disk image." If you didn't, you'll need to change the extension in the script.
- The password for the encrypted disk image saved in your OS X keychain.
- A newer version of rsync installed. I'm using version 3.1.1 from MacPorts. If you're using the stock rsync, you'll need to change the rsync line in the script (see notes).
- The terminal-notifier tool installed; my script uses it to send messages to the OS X Notifications system. (I discuss using it, and how to install it, in this article.)
Assuming you've got those things in place, here's the script. Note that this is not cut-and-paste ready to use; please read the in-script comments and edit as needed.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 | #!/bin/sh #################################################################### ### Replace all NAME-OF-DISK-IMAGE references with the actual ### ### name of your secure disk image. If the name contains spaces, ### ### remember to escape\ them\ with\ backslashes. ### ### ### ### Do the same for NAME-OF-ARCHIVE, too. ### #################################################################### # set the path to the folder with the encrypted disk image file SECUREDIR="/path/to/encrypted-disk-image/folder" # Mount the encrypted disk image ### Note: Leave "disk image password" as it appears! ### ### Do *not* replace it with the actual password ### ### to your disk image! ### security find-generic-password -w -D "disk image password" -l NAME-OF-DISK-IMAGE.sparsebundle | hdiutil attach $SECUREDIR/NAME-OF-DISK-IMAGE.sparsebundle sleep 3 # Check to make sure image mounted; notify if it failed ### The MOUNTED-IMAGE-NAME here is different than the name of your ### ### disk image file; it's the name you see in the Finder's sidebar ### ### when the disk image is mounted. ### [ -d /Volumes/MOUNTED-IMAGE-NAME ] || terminal-notifier -title "Alert!" -message "Disk image failed to mount" && exit 1 [ -d /Volumes/MOUNTED-IMAGE-NAME ] || exit 1 # Copy key files to disk image # If you're using the stock rsync, change -avzXE to -avE # rsync -avzXE "/path/to/some/important/files" "/Volumes/MOUNTED-IMAGE-NAME/folder1" rsync -avzXE "/path/to/other/key/files" "/Volumes/MOUNTED-IMAGE-NAME/folder2" rsync -avzXE "/different/path/to/other/files" "/Volumes/MOUNTED-IMAGE-NAME/folder3" # Repeat above as needed # Eject disk image hdiutil detach "/Volumes/MOUNTED-IMAGE-NAME" # Zip, then copy to cloud drive eval zip -r "$SECUREDIR"/NAME-OF-ARCHIVE.zip $SECUREDIR/NAME-OF-DISK-IMAGE.sparsebundle/ cp "$SECUREDIR"/NAME-OF-ARCHIVE.zip "/path/to/local/mirror/of/cloud/drive/" # Optional: remove the archive file when done # Remove the '#' in the next line to do so # rm "$SECUREDIR"/NAME-OF-ARCHIVE.zip # Send a message about it terminal-notifier -title "Back up done" -message "Key files encrypted and on your cloud drive" |
As noted, there are lots of paths to modify, and names to decide on, etc. So consider the script a template for your own use, and customize as necessary. (Remember to make it executable via chmod when ready to use.)
Note, too, that with the disk image password in your keychain, if someone gets access to your Mac (and its login and keychain passwords), then they'll have access to the encrypted disk image. But given this script is taking files that are currently not encrypted, that's a bit of a moot point.
The first time you run the script, you'll get a security dialog from OS X, asking about access to the saved keychain data. You want to make sure you click Always Allow:
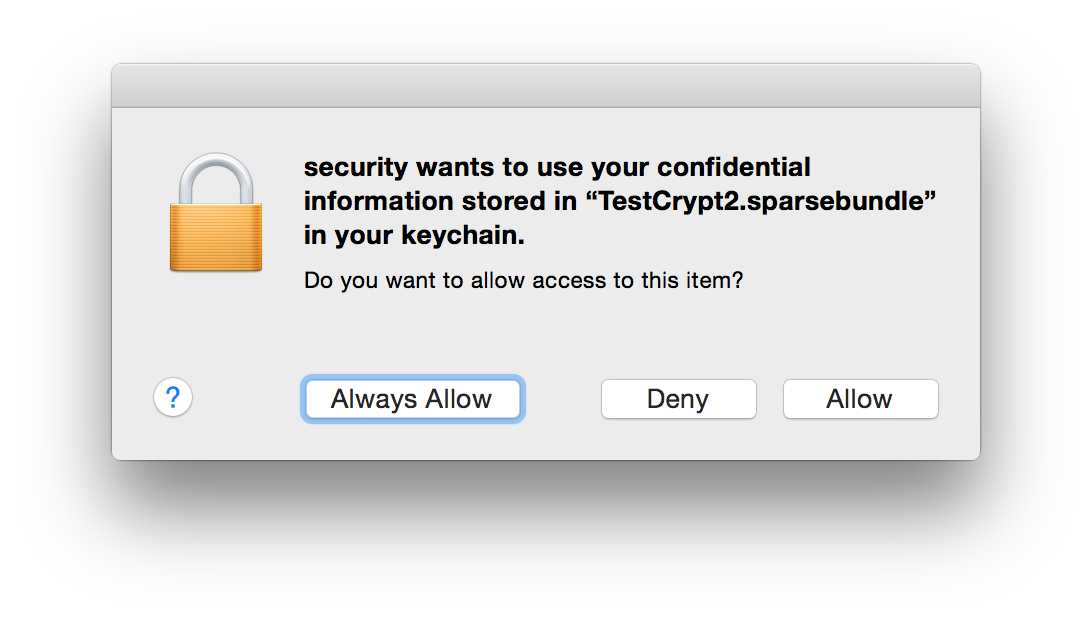
Once you've clicked that button once, you'll never see this dialog again.
To execute my script, I'm using a launchd agent that runs every night after I'm asleep—that way, I can be sure I don't have any of the files open. But I sleep soundly, knowing that our key files are backed up in the cloud about as safely as possible.
Rob, I use Viivo (https://viivo.com) to encrypt my cloud data. Concept is that you have to have two folders: one with the unencrypted files, the second (on Dropbox.com) is the encrypted files. The software watches the unencrypted folders for changes and makes the corresponding change on the encrypted folder in Dropbox.
I'd never heard of them; thanks for the pointer!
-rob.
Comments are closed.